Global Intrusion Detection and Prevention Systems Market - Comprehensive Data-Driven Market Analysis & Strategic Outlook
The global intrusion detection and prevention systems market is a segment of the overall cybersecurity industry, which is an area that protects networks and data from unauthorized access and malice activities. Its evolution started in the late 1980s and early 1990s when businesses began linking their internal systems to the internet. The initial tools were log analyzers that were very basic and mostly used by government and large research agencies. During that period, the majority of the online threats were in the form of experimental attacks conducted by curious programmers rather than organized criminals.
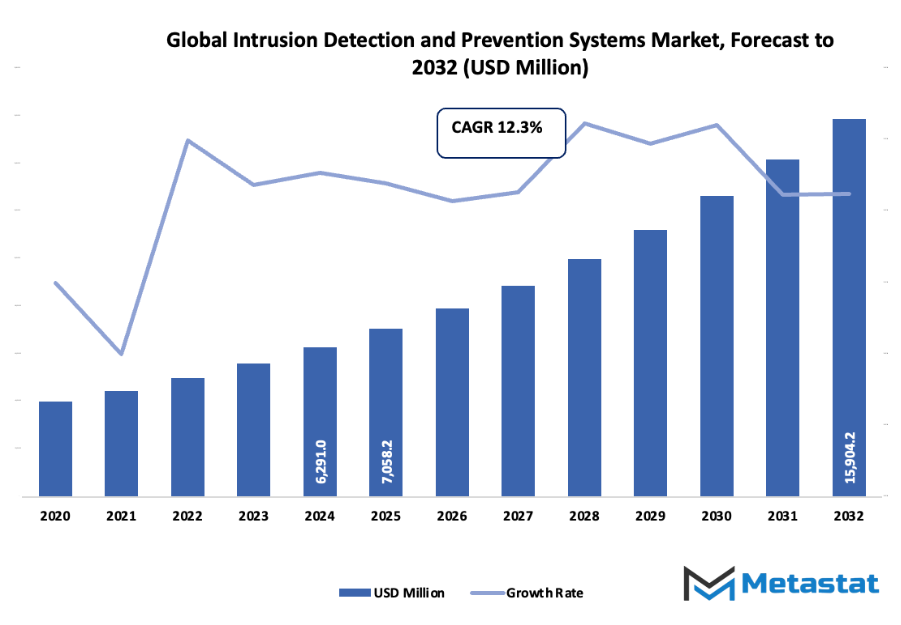
- The global intrusion detection and prevention systems market is expected to reach a valuation of around USD 7,058.2 Million by 2025, with a CAGR of around 12.3% through 2032, and a maximum value of over USD 15,904.2 Million in the future.
- On-Premises solutions take up almost the entire market share, and through heavy investment in research and development, they are the major force behind the introduction of new technologies and broadening of application areas.
- Some of the biggest factors leading to the increase in the market size are frequent and complex cyberattacks, and the need to comply with strict government regulations (e.g., GDPR, HIPAA) in the industry.
- The introduction of AI and ML, which will result in better detection of threats, is among the potential chances.
- It is a fact that the market is going to be worth much more in a decade's time and thus major growth areas will be opened up.
One of the primary shifts in perspective took place when digital attacks were recognized by businesses as a source of monetary loss and damage to image. A strong defense was needed, which was far beyond that of simple firewalls, hence the invention of methods for determining whether or not there was an intrusion which would notify the security crew when suspect traffic was detected. Later, the issue of aggressive and automated attacks came. Just sounding the alarms was inadequate, the technology to do it all by itself was the demand from business. This made way for the development of the systems that not merely detected but also prevented intrusions by blocking the bad traffic during the very moment it was coming in.
Cybercrime escalated along with the growth of the internet. Criminals went from one-off hacks to systematic frauds. As a countermeasure, vendors employed cutting-edge machine learning, vigorous traffic scrutiny, and user behavior monitoring. The regulatory environment consisting of GDPR and other similar rules for different financial sectors, made it a necessity for companies to go for advanced and powerful defenses. The scenario was different again when cloud computing became the way to go. The security tools were now required to be more than just boxes to be installed, they should be operating even in the dispersed areas.
The global intrusion detection and prevention systems market has turned over a new leaf as a vibrant area characterized by shifting customer aspirations. The businesses are no longer wanting to manually check an infinite number of alerts, rather, they prefer integration that is easy, deployment that is fast, and decision-making that is automated. The companies will be searching for solutions that are able to do traffic analysis over local area networks, data centers, and cloud infrastructures without affecting the performance of operations.
Before long, the prevention systems will be turned from the reactive kind to the predictive type. Various platforms will turn to AI for the prediction of the attack patterns and thus, not only will the digital assets be secured but also, humans will not have to be constantly involved.
Market Segments
The global intrusion detection and prevention systems market is mainly classified based on Deployment Mode, Type, Components, Vertical.
By Deployment Mode is further segmented into:
- On-Premises: The on-premises setup secures the entire infrastructure that is sensitive and related to security within the organization's premises. The hardware and software remain on the company's premises which facilitate strong control over the processes of data handling and monitoring. This arrangement is useful for companies that have very stringent regulatory requirements or those that have little trust in the security of the external hosting. Local control means that security actions are under direct supervision, hence supporting faster internal decisions.
- Cloud-based: The cloud-based deployment option routes through the remote servers which are operated by a third-party provider. This alternative not only eliminates the burden of heavy hardware costs but also facilitates the quick scaling of resources during high activity periods. Usually, updates are performed automatically without any manual handling, thus benefiting users with the continuous access of advanced security tools. A large number of small and medium enterprises prefer this deployment due to its flexible spending.
By Type the market is divided into:
- Network-based: Network-based systems consist of organization-wide infrastructure that looks after the traffic moving in and out by scanning the data and detecting harmful patterns. Sensors are used to keep an eye on the activity going in and out, which helps the security teams to find the threats before any huge damage is done. This technique is suitable for large networks with continuous movement of information and is preferred by many enterprises for extensive coverage.
- Wireless-based: Wireless-based systems are the ones keeping an eye on the traffic that gets transmitted over the wireless channels. This method is the one that companies put their trust on to make the data passing through the access points, routers, and connected devices safe. The system also checks for any unauthorized user who is trying to get into the network. This method has the potential to provide a strong security layer for the modern workplace, which is characterized by mobile devices and remote connections.
- Network Behaviour Analysis: Network Behaviour Analysis makes continuous observation over the patterns and actions taking place through the network paths. Unusual data transfer or sudden increase of activity will cause alarms to go off hence the method enables early threat detection. This approach also assists in discovering attacks that deliberately avoid common filters. The method is favored by many organizations for spotting the unpredictable actions that trigger the silent attacks in progress.
- Host-based: Host-based systems are deployed on one device only, either a workstation or a server. The system performs its checks mainly on logs, applications, and local files of the device to find out about any harmful actions. Host-based protection is commonly applied for securing high-value machines that contain confidential data in many firms. The method allows for the precise protection of individual devices that require strict monitoring.
By Components the market is further divided into:
- Solutions: Solutions comprise the primary instruments that detect and eliminate detrimental actions. These instruments are monitoring the traffic, analyzing the behavior, and preventing the risky actions. Complete solutions for stronger defense layers are often selected by many organizations. The adoption rate is often elevated during times of cybersecurity pressure leading the firms to the acquisition of automated protection systems for operating with more safety.
- Services: Services are the provision of assistance from professionals who are responsible for installation, monitoring, and maintenance support. The process of outsourcing takes away the internal burden and is beneficial for companies that have a small security team. Besides, services are also educating the staff about the right usage and the way to deal with threats. There are a lot of organizations that prefer to have a service plan that is ongoing to ensure that their protection methods are constantly improved and operation is never interrupted.
By Vertical the global intrusion detection and prevention systems market is divided as:
- Banking, Financial Services and Insurance (BFSI): The BFSI sector handles sensitive financial data, making strong protection essential. Systems watch transactions and network flow to stop fraud, breaches, and unauthorized access. Consistent security helps maintain trust among customers. Many financial firms invest heavily in advanced threat monitoring due to strict regulatory requirements and risk of financial loss.
- Government and Defense: Government and defense institutions manage confidential information that demands maximum protection. Strong prevention tools keep harmful actors away from classified networks. Systems support constant monitoring, helping protect national interests and critical infrastructure. High security requirements push these sectors to adopt advanced tools that reduce digital threats and unauthorized data extraction.
- Healthcare: Healthcare facilities store patient records and medical research, making these locations frequent targets. Security systems protect data passing between medical devices, databases, and cloud platforms. Any breach can disrupt treatments and damage trust. Hospitals and clinics strengthen cyber protection to support safe patient service and continuous medical operations.
- Information Technology (IT) and Telecom: IT and telecom firms handle huge data movement across networks and servers. Strong security tools keep harmful activity out of core systems. Fast detection helps prevent service disruption and communication breakdown. These industries rely on proactive defense to support smooth data transfer and safeguard customer information across multiple platforms.
- Retail and eCommerce: Retail and eCommerce businesses manage payment information and personal customer data. Security systems watch digital storefronts and payment gateways, reducing risks of unauthorized access. Faster detection lowers chances of stolen data and financial loss. Many merchants adopt prevention tools to build customer confidence and support secure online transactions.
- Manufacturing: Manufacturing companies depend on connected equipment and automated machinery. Security systems protect production lines from harmful interference and data extraction. Disruptions can lead to costly downtime and delivery delays. Cyber protection supports safe operations by guarding communication among systems, reducing threats that may target factory processes and supply networks.
- Others: Other sectors, including education, energy, and transportation, use these systems to secure valuable data and ensure safe daily operations. Security tools monitor networks, helping reduce downtime and block harmful interference. Adoption continues to grow as organizations understand the importance of preventive defense to avoid financial loss and protect sensitive information.
|
Forecast Period |
2025-2032 |
|
Market Size in 2025 |
$7,058.2 Million |
|
Market Size by 2032 |
$15,904.2 Million |
|
Growth Rate from 2025 to 2032 |
12.3% |
|
Base Year |
2024 |
|
Regions Covered |
North America, Europe, Asia-Pacific, South America, Middle East & Africa |
By Region:
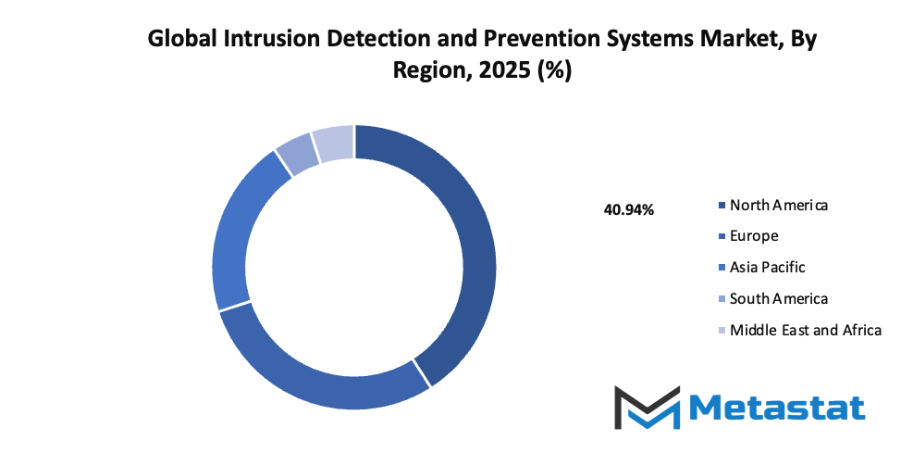
- Based on geography, the global intrusion detection and prevention systems market is divided into North America, Europe, Asia-Pacific, South America, and the Middle East & Africa.
- North America is further divided into the U.S., Canada, and Mexico, whereas Europe consists of the UK, Germany, France, Italy, and the Rest of Europe.
- Asia-Pacific is segmented into India, China, Japan, South Korea, and the Rest of Asia-Pacific.
- The South America region includes Brazil, Argentina, and the Rest of South America, while the Middle East & Africa is categorized into GCC Countries, Egypt, South Africa, and the Rest of the Middle East & Africa.
Growth Drivers
- Increasing Frequency and Sophistication of Cyberattacks:
Growing digital activity across businesses encourages greater attempts by unauthorized actors to access valuable data. Rising attack methods require faster threat recognition and rapid intervention. Demand for stronger prevention tools supports rising adoption within the global intrusion detection and prevention systems market. Constant monitoring helps reduce financial loss, protects reputation, and supports secure business operations.
- Stringent Regulatory Compliance Requirements (e.g., GDPR, HIPAA):
Government and industry rules require protection of sensitive records. Regulations focus on responsible data handling, security controls, and clear reporting of breaches. Adoption of reliable detection and prevention solutions helps maintain compliance, avoid heavy penalties, and provide higher trust for customers, partners, and stakeholders within various business environments.
Challenges and Opportunities
- Complexity of Implementation and Management:
Installation and ongoing handling of detection and prevention solutions demand skilled expertise, careful system alignment, and continuous maintenance. Extensive setup time and resource allocation cause hesitation for some organizations. High technical requirements often lead to increased operational costs, making adoption difficult for smaller businesses with limited security budgets.
- False Positives and Negatives Leading to Alert Fatigue:
Security tools sometimes generate unnecessary warnings or miss genuine threats. Excessive alerts reduce focus and delay action on real security risks. Missed alerts allow malicious activity to continue unnoticed. Constant monitoring pressure lowers performance, slows response time, and increases vulnerability to harmful network activity.
Opportunities
Integration of Artificial Intelligence and Machine Learning for Enhanced Threat Detection:
Advanced data analysis supports faster recognition of suspicious activity. Automated learning identifies patterns and predicts harmful actions before damage occurs. Continuous improvement within detection engines reduces unnecessary alerts and strengthens accuracy. Adoption encourages stronger protection, higher efficiency, and greater confidence in long-term cybersecurity planning.
Competitive Landscape & Strategic Insights
The competitive landscape of the global intrusion detection and prevention systems market shows strong activity from well-established global corporations and rising regional organizations. Major participants such as Cisco Systems, Inc., IBM Corporation, Palo Alto Networks, Inc., Check Point Software Technologies Ltd., Fortinet, Inc., Trend Micro, Inc., McAfee, LLC, AT&T Inc., Broadcom Inc., Juniper Networks, Inc., F5 Networks, Inc., SecureWorks Corp., Trustwave Holdings, Inc., Armor Cloud Security, Hilstone Networks, Rapid7, Inc., SolarWinds Corporation, NSFOCUS, AlertLogic, Vectra, and WatchGuard guide the direction of this sector. Each organization brings unique technology and long-term strategies, creating constant competition and steady progress.
Long-standing global corporations often focus on broad portfolios and strong research programs. These groups direct substantial funding toward product enhancement, large customer support networks, and advanced security features. Strong brand recognition helps these leaders secure large enterprise partnerships, government contracts, and large-scale digital security projects. Consistent development, reliable service, and rapid response to new threats allow these companies to maintain a strong position in the overall market.
Regional organizations, on the other hand, often focus on flexible pricing and tailored solutions. Close relationships with local businesses create opportunities for faster decision cycles and direct feedback from customers. A focus on customization and quicker updates allows many regional organizations to compete with much larger corporations. Growing interest in cloud-based security, automated monitoring, and artificial intelligence encourages even newer entries to invest in innovative approaches that deliver faster and more accurate threat handling.
Market size is forecast to rise from USD 7,058.2 Million in 2025 to over USD 15,904.2 Million by 2032. Intrusion Detection and Prevention Systems will maintain dominance but face growing competition from emerging formats.
Demand for stronger defensive measures continues to rise as more devices and networks connect to online activity. Business sectors such as banking, healthcare, and public services rely heavily on digital safety. Continuous development from major corporations and smaller regional organizations encourages smarter technology and more dependable protection methods within the global intrusion detection and prevention systems market.
Report Coverage
This research report categorizes the global intrusion detection and prevention systems market based on various segments and regions, forecasts revenue growth, and analyzes trends in each submarket. The report analyses the key growth drivers, opportunities, and challenges influencing the global intrusion detection and prevention systems market. Recent market developments and competitive strategies such as expansion, type launch, development, partnership, merger, and acquisition have been included to draw the competitive landscape in the market. The report strategically identifies and profiles the key market players and analyses their core competencies in each sub-segment of the global intrusion detection and prevention systems market.
Intrusion Detection and Prevention Systems Market Key Segments:
By Deployment Mode
- On-Premises
- Cloud-based
By Type
- Network-based
- Wireless-based
- Network Behaviour Analysis
- Host-based
By Components
- Solutions
- Services
By Vertical
- Banking, Financial Services and Insurance (BFSI)
- Government and Defense
- Healthcare
- Information Technology (IT) and Telecom
- Retail and eCommerce
- Manufacturing
- Others
Key Global Intrusion Detection and Prevention Systems Industry Players
- Cisco Systems, Inc.
- IBM Corporation
- Palo Alto Networks, Inc.
- Check Point Software Technologies Ltd.
- Fortinet, Inc.
- Trend Micro, Inc.
- McAfee, LLC
- AT&T Inc.
- Broadcom Inc.
- Juniper Networks, Inc.
- F5 Networks, Inc.
- SecureWorks Corp.
- Trustwave Holdings, Inc.
- Armor Cloud Security
- Hilstone Networks
- Rapid7, Inc.
- SolarWinds Corporation
- NSFOCUS
- AlertLogic
- Vectra
- WatchGuard
WHAT REPORT PROVIDES
- Full in-depth analysis of the parent Industry
- Important changes in market and its dynamics
- Segmentation details of the market
- Former, on-going, and projected market analysis in terms of volume and value
- Assessment of niche industry developments
- Market share analysis
- Key strategies of major players
- Emerging segments and regional growth potential





 US: +1 3023308252
US: +1 3023308252






